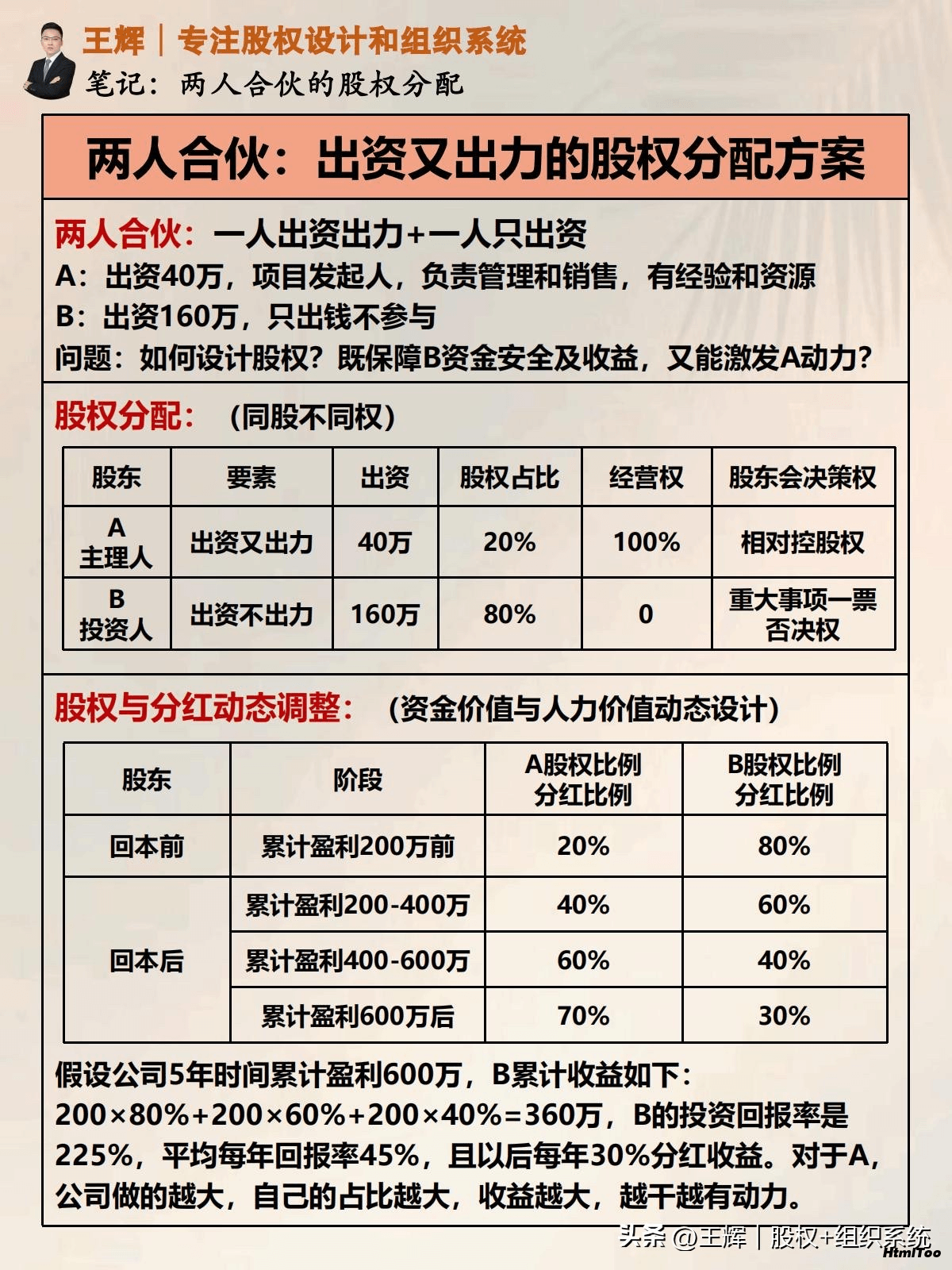
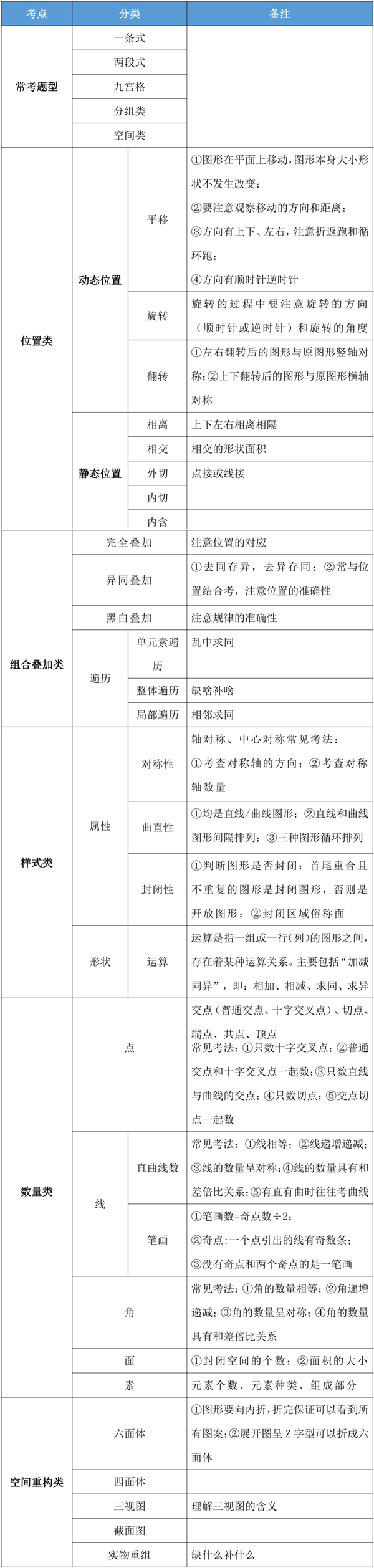
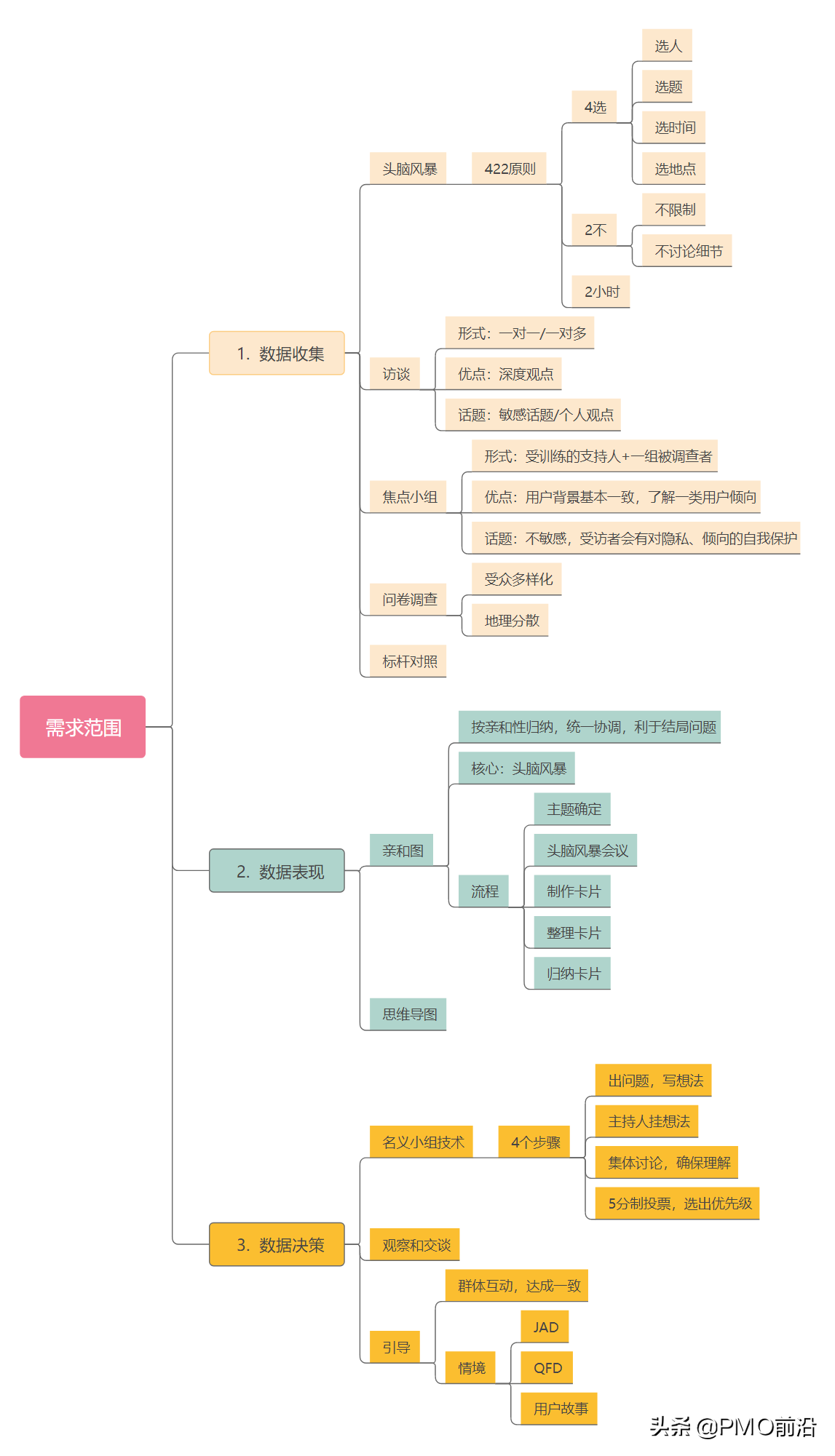
Blackbox_exporter概述
blackbox exporter是允许在HTTP, HTTPS, DNS, TCP and ICMP等协议的端点进行黑盒探测的采取器
官方github: https://github.com/prometheus/blackbox_exporter
Blackbox_exporter 部署
blackbox exporter二进制部署
获取包
创建用户
服务启动脚本
启动服务
docker方式部署
blackbox_exporter configure
配置文件为/etc/blackbox_exporter/blackbox.yml
blackbox_exporter通过配置文件和命令行标志(例如要加载什么配置文件,监听哪个端口以及日志记录格式和级别)进行配置。
同时可以运行时动态的重新加载配置文件,当重新加载配置文件失败时,不影响在运行的配置
重载方式:curl -XPOST http://127.0.0.1:9115/-/reload
blackbox_exporter 的超时时间由Prometheus配置中的scrape_timeout自动确定,略微减少以允许网络延迟.默认是10s
示例配置:
https://github.com/prometheus/blackbox_exporter/blob/master/example.yml
监控http
一般情况下都会以非root用户运行blackbox_exporter,Wie了使用icmp prober,需要设置CAP_NET_RAW,即对可执行文件blackbox_exporter执行下面的命令:setcap cap_net_raw+ep /usr/local/bin/blackbox_exporter
prometheus configure
参考
http://blog.fleeto.us/content/kubernetes-blackbox-shi-xian-dui-web-he-dns-de-jian-dan-jian-kong
https://github.com/prometheus/blackbox_exporter/blob/master/CONFIGURATION.md
上篇:
万能数据收集器 Fluentd
下篇:
Consul+Prometheus系统监控之注册发现
1 大模型无非就这点东西 2 一天做出短剧App:我的MCP极速流 3 我用ai员工自动运营Google,登顶并收8k美金 4 网络故障秒排指南:10 个实战命令从入门到精通 5 男人若想发大财,就莫要去打工,我推荐做这二十件事。 6 运维必备:掌握这3个存储技术 7 win11 连接共享打印机报错:0x00000040 或者 .709或者 .11... 8 7大热门Agent框架盘点:助你轻松构建多智能体AI应用 9 IT运维服务方案V3.0【拿来即用】 10 Thumoon:Python图像处理的高效利器,快速上手指南 11 从 0 到 1:使用 Loki + Promtail + Grafana 搭建日... 12 使用Easy Dataset为大模型准备训练数据,在线部署